Scenario :
CoCanDa, a planet known as ‘The Heaven of the Universe’ has been having a bad year. A series of riots have taken place across the planet due to the frequent abduction of citizens, known as CoCanDians, by a mysterious force. CoCanDa’s Planetary President arranged a war-room with the best brains and military leaders to work on a solution. After the meeting concluded the President was informed his daughter had disappeared. CoCanDa agents spread across multiple planets were working day and night to locate her. Two days later and there’s no update on the situation, no demand for ransom, not even a single clue regarding the whereabouts of the missing people. On the third day a CoCanDa representative, an Army Major on Earth, received an email.
Inventories : Email File with password ‘btlo’
PROCEDURE
The email file was subjected for analysis , a password is required to the open the file which was given ‘btlo’. The email contain detailed information which is extracted from ‘original message’. This message carry primary information about the sender details. Let’s analyse the email.



Recipient Information
- Delivered-To:
themajoronearth@gmail.com - Indicates that the recipient of this email who is this mail intended to.
Received by (SMTP IDs):
- The email was received by Google’s servers (
2002:a92:bd02:0:0:0:0:0) with the SMTP IDc2csp3604485ile. - Multiple
Receivedheaders trace the email's path from the original sender's server to the recipient’s inbox, showing it passed through different servers. And this server was the closest server to the recepient location.
Received from emkei.cz :
emkei.czis listed as the originating server. This site is known for providing an anonymous email service, which could indicate the email was sent through a potentially spoofed or anonymous platform. This server IP and hostname (93.99.104.210) might suggest that the sender is attempting to hide their identity.
SPF :
- Result:
spf=fail (google.com: domain of billjobs@microapple.com does not designate 93.99.104.210 as permitted sender) - The SPF record indicates a failed check. This means that although the email claims to be from
billjobs@microapple.com, Google flagged the email as not originating from an authorized server for the domainmicroapple.com. This suggests the email is likely spoofed, as it originates from an IP not associated with the alleged sending domain.
Sender Information
From: "Bill" <billjobs@microapple.com>
The email appears to be from “Bill” at billjobs@microapple.com, which is likely spoofed based on SPF failure. The address also mimics a blend of “Microsoft” and “Apple,” possibly to mislead recipients by implying a connection to reputable companies.
Reply-To: negeja3921@pashter.com
The “Reply-To” field is different from the “From” field, suggesting the sender wants replies directed to a different address. This is common in phishing or spoofed emails to avoid detection on the main sender address. This is the sign of poorly created phishing email.
Investigation
After analyzing the email header, our next steps are to investigate the source and purpose of this email. The sender attached two files, and our analysis begins by decoding the first attachment, which is in Base64 format. For this, we’ll use the tool CyberChef.
How to Use CyberChef
- Open CyberChef.
- Paste the Base64-encoded input.
- Select and drag the ‘From Base64’ operation to the Recipe section.
- View the decoded text, which reveals details about the victim(s).
- Save the output as a attachment.txt file for further examination.

Analyzing the Second Attachment
The sender’s message mentioned solving a puzzle using an attachment. This attachment was marked as a PDF but was also in Base64 format. After decoding it in CyberChef, we discovered it provided no clear information.

To further investigate, we converted it to hexadecimal (hex) to identify its file type using GCK’s File Signatures Table. The file’s hex signature starts with 50 4B 03 04, identifying it as a .zip file.


Extracting the Contents of the .zip File
- Save the decoded output with a
.zipextension. - Extract the contents of the
.zipfile.
The extracted folder now contains two files. Upon inspecting for hidden files, we found a file named money.xlsx.


Analyzing the Files Inside the Zip
To further analyze the files, we use HxD, a hex editor.
- Open each file in HxD to inspect its hex code and verify its format.
2. For the first file, “DaughtersCrown,” the hex code identified it as a JPEG image file.Rename the file with a .jpeg extension to view the image.



3. The second file, “GoodJobMajor,” has a hex signature indicating it is a PDF.


4. Rename it with a .pdf extension to access its contents.

5.The third file, money.xlsx, is already labeled as an Excel file.
Examining the Excel File
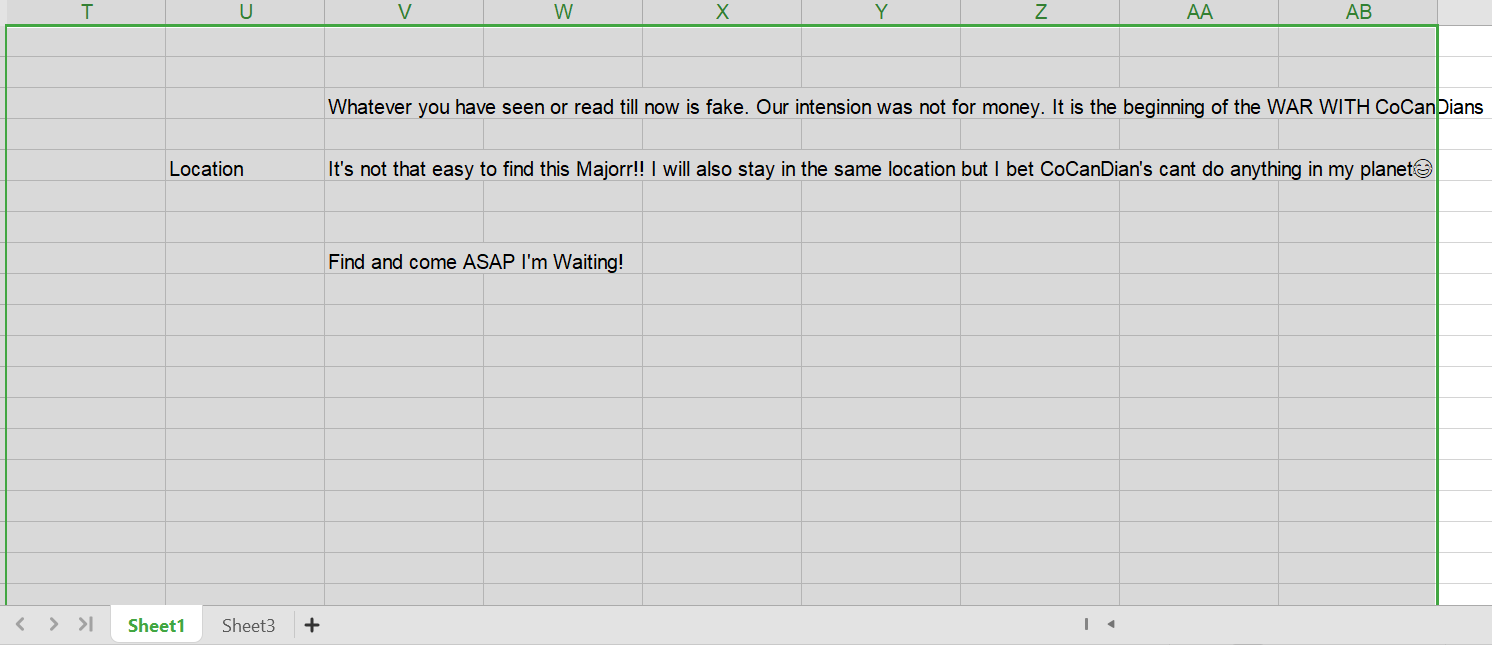
The Excel file contains two sheets: one with visible data and a second blank sheet, which raises suspicion. A common technique for hiding data is using white text on a white background.
To reveal any hidden data:
- Select the entire second sheet, choose Clear Content, then Format.
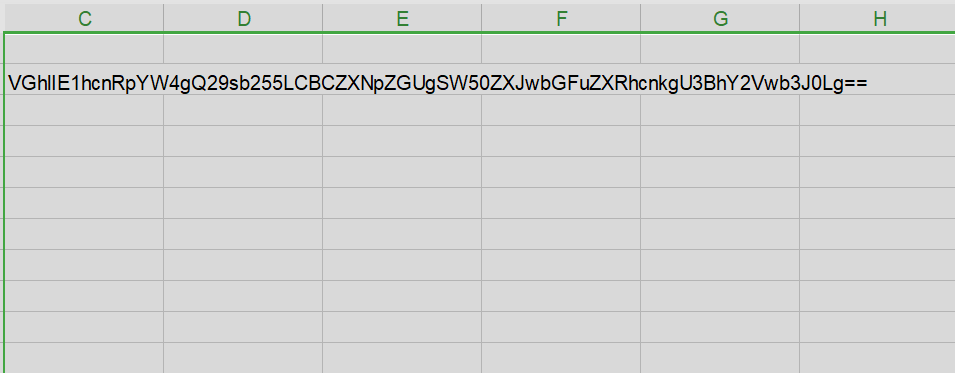
- This reveals hidden information encoded in Base64 format
Decoding the Hidden Information
Copy the hidden Base64 text, paste it back into CyberChef, and apply the ‘From Base64’ operation to decode it to its original text.The hidden text revealed the exact location of the sender.

Summary
We have now successfully identified and investigated all files from the email, uncovering hidden messages and decoding relevant information. This investigation highlights the layered techniques often used in malicious emails, demonstrating the importance of thorough analysis.
Lets answer the questions in challenge
- emkei.cz.
emkei.cz is often used for anonymous email sending, suggesting the sender is concealing their identity.


Above image -shows that the email was received from emkei.cz email provider .

3. .zip

.zip is the filetype of the received attachment which helped to continue the investigation to identify the location.
4.Pestero Negeja

In order to identify the real name of the author, use exiftool to extract the metadata of attachment file .
5. The Martian Colony, Beside Interplanetary Spaceport

6.pashter.com

